Connecting OPC UA Publisher to Amazon AWS IoT with MQTT
26.11.2021
The following article was prepared together with Jan Borch who works as an IoT Solution Architect at Amazon Web Services. He has verified the concept and is also available for more details related to the AWS IoT platform.
Introduction
The OPC UA PubSub specification adds a publish-subscribe communication pattern to OPC UA applications. The primary advantage of this communication pattern is to decouple the message producer from the consumer. Producer and consumer do not need to know about each other to exchange messages, and multiple consumers can process each published message independently. To achieve this, the OPC UA PubSub specification introduces the concept of a message broker that dispatches the messages. The specification supports two transport protocol types: datagram transport, using UDP, and broker transport, using MQTT or AMQP. This guide will focus on the latter and uses AWS IoT Core as an MQTT compliant message broker.
The guide showcases the common industrial IoT use case to publish data from OPC UA servers running at the industrial edge to applications running in the cloud to perform big data analytics or predictive maintenance.
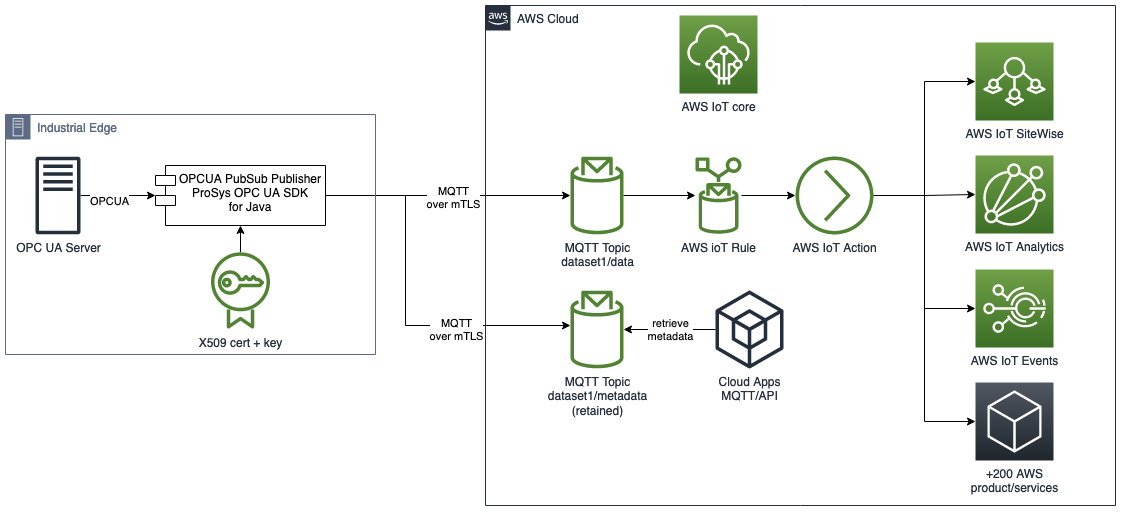
The OPC UA Publisher connects to AWS IoT Core using MQTT over secure mTLS. It then starts publishing JSON encoded data and meta data. AWS IoT Core uses X.509 security certificates to authenticate the OPC UA Publisher. Once data lands in the AWS Cloud, the AWS IoT Core rule engine can be used to forward the messages to a downstream cloud application, a time series database such as Amazon Timestream or an AWS service such as AWS IoT SiteWise, AWS IoT Events, AWS IoT Analytics or one of the other 25 supported AWS service integrations.
Prerequisites
- AWS Account
- Prosys OPC UA SDK for Java 4.6.2 or later
- openssl
- AWS CLI
AWS IoT setup
In this guide, we will use the SamplePublisherServer application that is shipped with the Prosys OPC UA SDK for Java. This sample starts an OPC UA Server, and additionally configures an OPC UA Publisher that publishes an OPC UA variable at regular intervals to an MQTT broker, such as the AWS IoT Core.
Before starting the sample we need to retrieve the AWS IoT Core MQTT endpoint for your AWS account, you can use the AWS CLI for this:
aws iot describe-endpoint --endpoint-type iot:DATA-ATS
{
"endpointAddress": "xxxx-ats.iot.eu-west-1.amazonaws.com"
}
Write down the exact endpoint that is printed out - you will need it later.
We also need to use the CA certificate of the AWS IoT endpoint. We can retrieve it with:
curl https://www.amazontrust.com/repository/AmazonRootCA1.pem
> AmazonRootCA1.pem
AWS IoT Core uses IoT policies to control the access to the AWS IoT Core MQTT endpoint and MQTT topic. We need to define an AWS IoT policy to allow the OPC UA Publisher to connect to AWS IoT.
So, store the following policy into a file called pubSubPolicy.json
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"iot:Connect"
],
"Resource": [
"arn:aws:iot:*:*:client/*"
]
},
{
"Effect": "Allow",
"Action": [
"iot:Publish",
"iot:RetainPublish"
],
"Resource": [
"arn:aws:iot:*:*:topic/prosysopc/sample/*"
]
},
{
"Effect": "Allow",
"Action": [
"iot:Receive"
],
"Resource": [
"arn:aws:iot:*:*:topic/prosysopc/sample/*"
]
}
]
}
and execute the following command to create the IoT policy:
aws iot create-policy
--policy-name prosyspubsubpolicy
--policy-document file://./pubSubPolicy.json
Now we are all set to execute the Sample Publisher Server.
Start the Prosys OPC UA Sample Publisher Server
The easiest way to start the sample publisher is to use the provided
shell or BAT scripts samplepublisherserver.sh or
samplepublisherserver.bat and replace <Your AWS IoT Endpoint> with your
AWS IoT endpoint you retrieved in the previous section.
samplepublisherserver.sh
--encoding json
--address ssl://<Your AWS IoT Endpoint>:8883
--ca-cert AmazonRootCA1.pem
NOTE: ‘–ca-cert’ is a new command line argument that needs to be added to the SamplePubSubConfiguration class in the sample project, in addition to a definition of a SocketFactory. You can use the following patch to modify the sample like this.
At the first invocation, the sample application will first create a
new self-signed OPC UA Application Instance Certificate that is used
to authenticate itself in OPC UA Client/Server communication. The
certificate is stored in the PKI/CA/private directory together
with the respective private key.
We will now use the Application Instance Certificate to also authenticate the Publisher with the AWS IoT endpoint.
This will, of course, fail on the first connection attempt, because the certificate is not trusted by the AWS IoT by default.
Stop the server by hitting ‘x ENTER’
If you check the log file SamplePublisherServer.log, you should see an
error message indicating that AWS IoT refused the connection:
Failed to connect to MQTT server ssl://xxxx-ats.iot.eu-west-1.amazonaws.com:8883 Connection lost (32109)
So, let’s register the Application Instance Certificate with AWS IoT.
First, navigate to the directory, where the sample stored the generated certificate:
cd PKI/CA/private
AWS IoT Core requires a certificate in PEM format, but the Prosys sample generates a DER-encoded certificate file, so we need to convert it accordingly before importing. You can use openssl for the conversion, as follows:
openssl x509
-inform der
-in SamplePublisherServer@YOURHOSTNAME_2048.der
-out SamplePublisherServer@YOURHOSTNAME_2048.crt
Replace YOURHOSTNAME with your computer’s actual hostname.
Next, import the certificate into AWS IoT:
aws iot register-certificate-without-ca
--certificate-pem file://SamplePublisherServer@YOURHOSTNAME_2048.crt
--status ACTIVE
--output text
--query 'certificateArn'
arn:aws:iot:eu-west-1:123456789012:cert/ababababab
Copy the Amazon Resource Name (ARN) of the certificate that is printed out, since we need it in the next command to attach the IoT policy to the certificate.
aws iot attach-policy
--policy-name prosyspubsubpolicy
--target arn:aws:iot:eu-west-1:123456789012:cert/ababababab
Restart the sample app and verify that you see ` - PubSubSystem started` in the log files.
Review the published message in the AWS IoT console
Open the AWS IoT console and navigate to the MQTT test client and
subscribe to the prosysopc/sample/data and
prosysopc/sample/metadata topics. You should now see the published
message in the MQTT Test client.
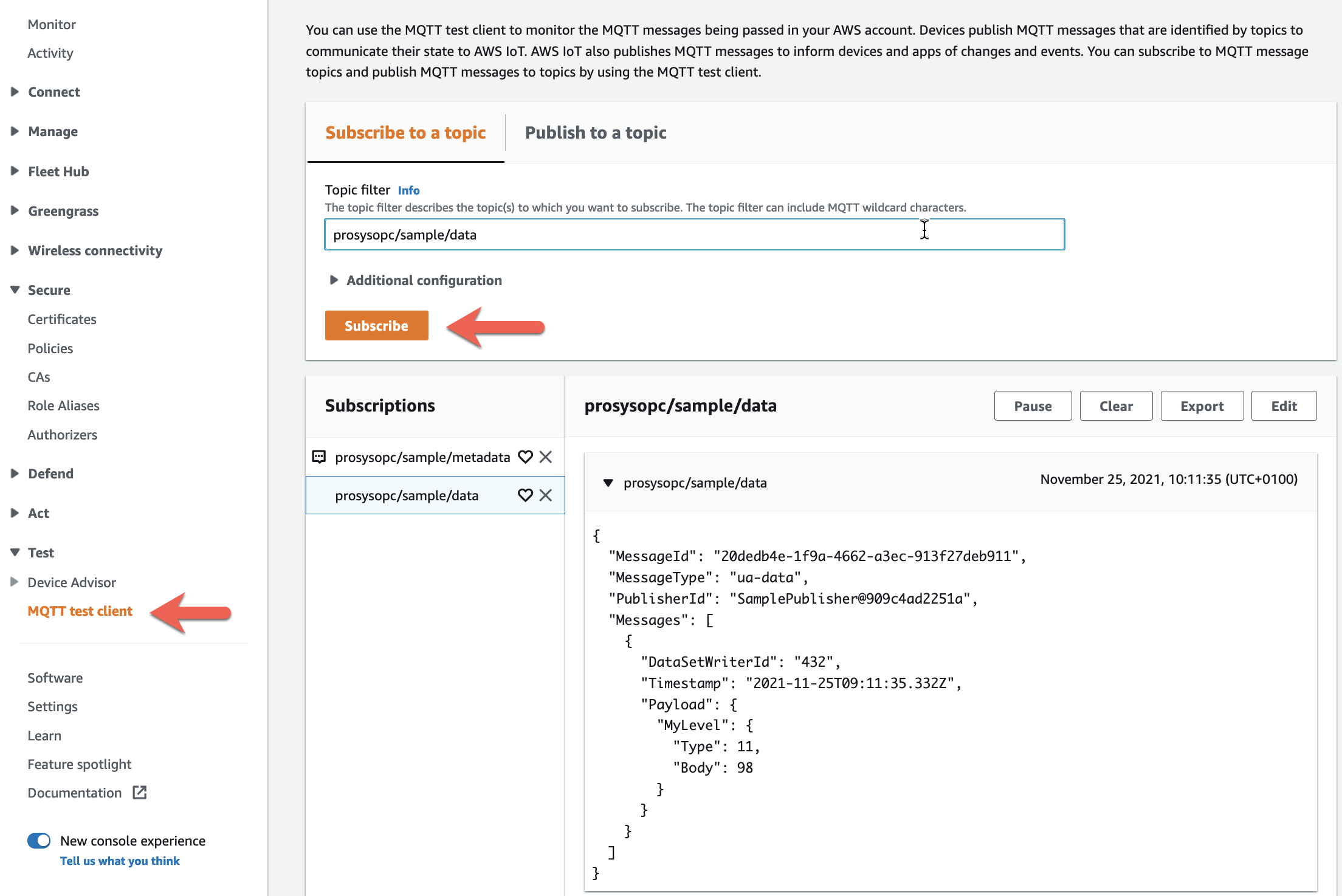
The metadata describes the Dataset format and can be used by the downstream application to decode the message payload. The metadata is published with the MQTT retained flag turned on, so the last message is persisted by AWS IoT Core for this topic.
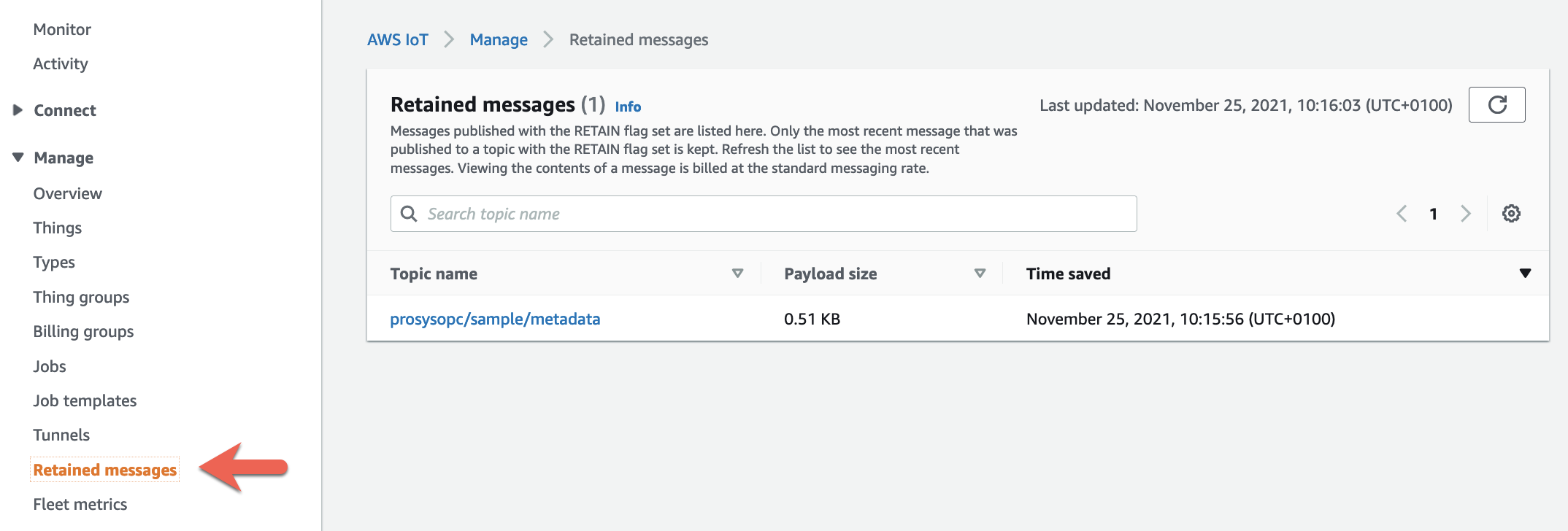
This allows the downstream application to retrieve the Dataset metadata and infer the message format before consuming messages. The application can subscribe over MQTT to the metadata topic to retrieve the retained message or can call the AWS IoT API to retrieve the retained message.
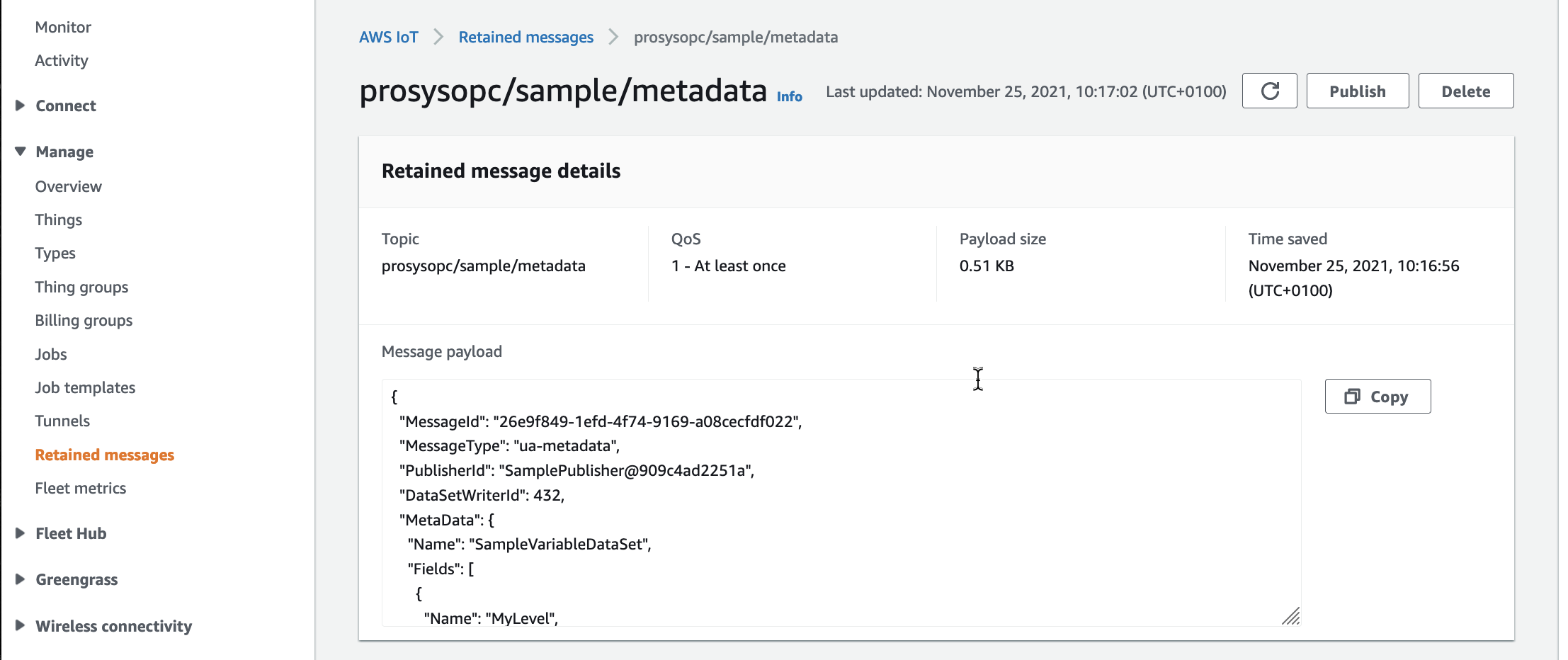
With the AWS CLI, use the following command:
aws iot-data get-retained-message
--topic prosysopc/sample/metadata
--query payload
--output text
| base64 -d
{
"MessageId": "1f15cee9-4163-449f-b2ac-c1f17af87714",
"MessageType": "ua-metadata",
"PublisherId": "SamplePublisher@909c4ad2251a",
"DataSetWriterId": 432,
"MetaData": {
"Name": "SampleVariableDataSet",
"Fields": [
{
"Name": "MyLevel",
"BuiltInType": 11,
"DataType": {
"Id": 11
},
...
Conclusion
In this guide, we learned how we can securely connect an OPC UA Publisher developed with the Prosys OPC UA SDK for Java to AWS IoT. To secure the communication between the publisher and AWS IoT, we leverage the built-in security concepts of OPC UA and more precisely the application identification mechanism using public certificates. And finally, we showcased how a downstream OPC UA Subscriber can retrieve the OPC UA PubSub Dataset metadata using the MQTT retained topics.
The AWS IoT rule engine can now be used to forward the published messages to downstream applications for further processing and analytics. The applications can be purpose-built databases like Amazon Timestream or IoT specific services, such as AWS IoT SiteWise, AWS IoT Events or AWS IoT Analytics.

Jouni Aro
Chief Technology Officer
Email: jouni.aro@prosysopc.com
Expertise and responsibility areas: OPC & OPC UA product development, project work and customer support
Tags: AWS, IoT, Cloud, OPC UA, PubSub, MQTT, Java, SDK for Java, Demo
comments powered by DisqusAbout Prosys OPC Ltd
Prosys OPC is a leading provider of professional OPC software and services with over 20 years of experience in the field. OPC and OPC UA (Unified Architecture) are communications standards used especially by industrial and high-tech companies.
Newest blog posts
Why Do Standards Matter in Smart Manufacturing?
The blog post discusses the importance of standards in smart manufacturing, envisioning a future where auto-configurable systems in manufacturing rely on standardized data formats for seamless integration and reduced costs, with a focus on the OPC UA standard family as a key enabler.
OPC UA PubSub to Cloud via MQTT
Detailed overview of the demo presented at the OPC Foundation booth
SimServer How To #3: Simulate data changes on a server using an OPC UA client
A two-part step-by-step tutorial on how to write data changes on an OPC UA server using an OPC UA client.
