Securing automation networks in Industry 4.0 world
14.07.2022
The discussion about the Industrial Internet started fifteen years ago, and it was the launch of a new trend that IT systems began to utilise in large-scale data from automation and production. The better view of production enabled new ways to optimise sourcing, delivery, and production. This trend is also called the Fourth Industrial Revolution, aka Industry 4.0, which has been the leading driver of the automation world since then.
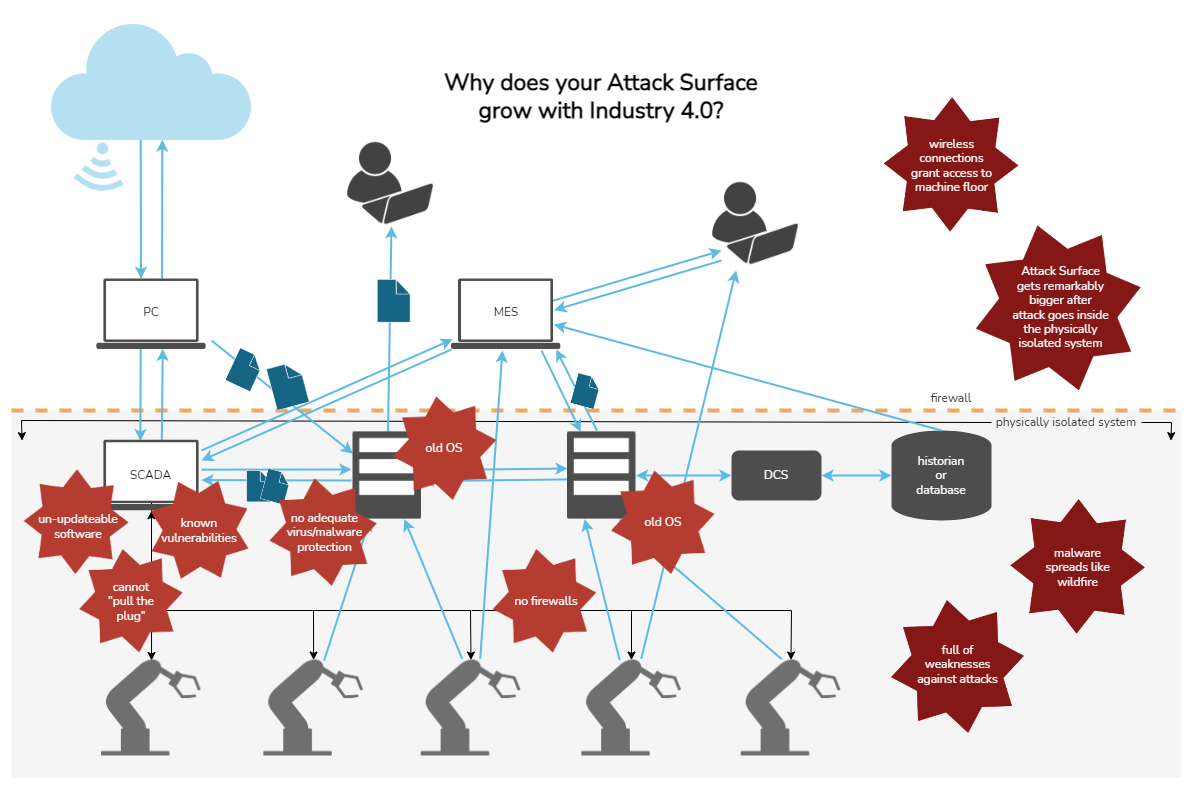
While Industrial Internet and Industry 4.0 enabled companies to act significantly more productively than before, it also made their physically isolated automation networks vulnerable to cyber-attacks. This started the work toward better security in automation, as the protective actions differ quite a bit from the standard IT security. In automation, you cannot update the operating systems very frequently, so known vulnerabilities exist, you may not install anti-virus by default to all computers, and you may need to run old computers that have even older Windows versions like XP, NT, and so on installed.
For over a decade, we have participated in initiatives such as Coreq-Ve and Kyber-Teo programs funded by the Finnish National Emergency Supply Agency to find the best practices for automation network protection. We also monitor the security work of the organisations we are included in, such as the OPC Foundation and the Industry 4.0 Alliance. Based on this knowledge, we have collected some essential tips to make your automation network attack surface as minimal as possible while still utilising all the opportunities of Industry 4.0.
Minimise your automation network attack surface with these three basic rules:
- Use OPC UA when crossing the network borders.
- Use an aggregating OPC UA server and a DMZ network between automation and other networks.
- Never allow remote access directly to the automation network computers.
1. Use OPC UA when crossing the network borders
While using firewalls you may restrict the access to certain networks easily, to minimize the attack surface of certain networks it’s important to use secure communication between different networks with different characteristics. OPC UA enables a standard, widely supported, yet very secure way to communicate compared to the propriety automation protocols or IT protocols, such as REST/JSON or propriety payload MQTT.
The inbuilt security features include six out of seven traditional security aspects:
- Confidentiality
- Integrity
- Availability (partly)
- Authentication
- Authorization
- Auditability
Non-Repudiation is the only aspect that is not inbuilt into the OPC UA specification.
Availability is also always a challenge as protection against DoS attacks should be done in the layer above the service. By using OPC UA applications built with reputable commercial SDKs that are tested periodically against denial-of-service vulnerabilities and by limiting the access to the services in a minimum using the hints introduced later in the blog, the level of guaranteed availability is also very high.
We suggest that when accessing the automation network from any other network for data transfer purposes, only OPC UA with security enabled would be used. This especially applies to any access to the automation network.
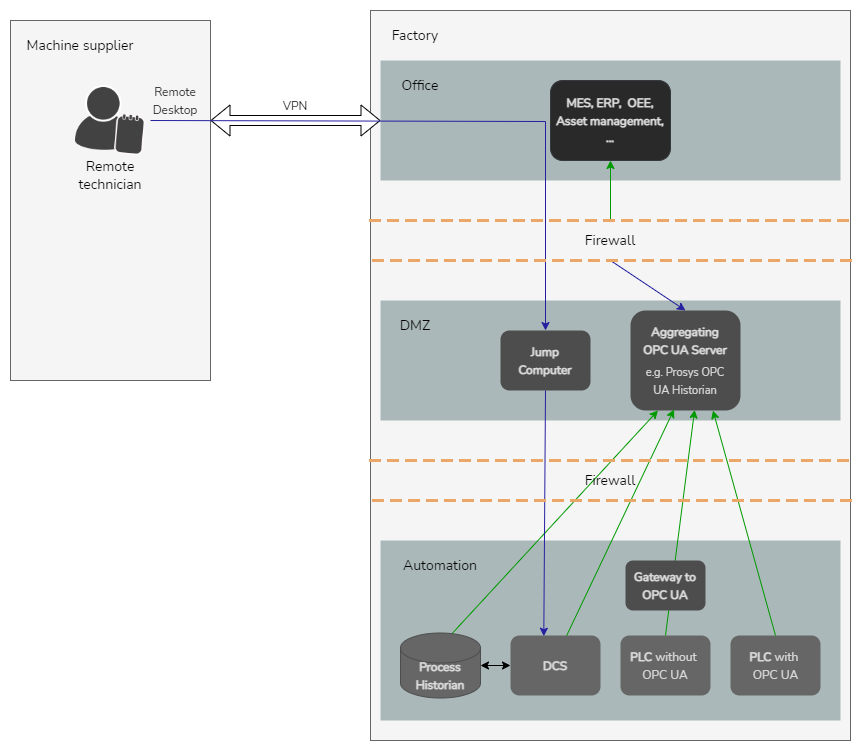
2. Use an aggregating OPC UA server and a DMZ network between automation and other networks
The reality of the OPC UA implementation projects on factory floors is that not all PLCs, machines, and devices have high-quality OPC UA servers that implement all security. The OPC UA specification does not even require security to be implemented on the smallest embedded servers that just do not have enough resources to do the encryption calculation.
To enable the use of OPC UA with security, another proxy server needs to be installed in between the source server and the network border. Since adding many of such servers makes the setup very complex, a better solution has been invented. The solution is to create a separate network segment, which we call the DMZ network, between the automation and other networks and to place there an aggregating OPC UA server that connects all OPC UA servers in the automation network and combines their data under one OPC UA server.
The DMZ network and an aggregating OPC UA server also simplify the firewall configuration to the extreme, while only single IP and Port needs to be opened towards northbound.
3. Never allow remote access directly to the automation network computers
Once you have implemented smooth dataflow from the OT to IT, as well as use OPC UA and firewall restricted the access to very secure use of OPC UA, it’s time to harden the typically still existing remote maintenance access to the vulnerable factory floor computers.
While having remote and maintenance access to the machines are typically a must for smooth production recovery in many breakdown cases, these accesses should be also made as secure as possible. So instead of giving any direct access from personal laptops or PCs to the computers in the automation network, set up dedicated jump machines to the DMZ network. These machines are hardened in general and specifically run the latest versions of the operating systems and anti-virus applications. All remote access is made using such machines as the middle point, e.g., remote desktop session to the jump computer and another remote desktop session from the jump computer to the target computer. Also, all files must be transferred to the jump computer before they can be further moved to the automation network computers.
Of course, this type of setup is not 100% safe, but it prevents many possible cases in which viruses or malware would have been able to infect the automation network machine.
Further improvements
In addition to these three basic rules, we advise our customers to implement, there are plenty of more advanced ways for protection; however, those depend on customer’s size and needs. Still making further network segmentation is reasonable in many cases. Whitelisting processes is very tricky and time-consuming, but once done correctly, it’s a very effective way to protect computers. Sometimes data diode might be used, but there is much more as well.
In case you are interested in hearing more about what we could do to enable standardised, harmonised, and secure integration of OT and IT, feel free to contact us!

Pyry Grönholm
CEO
Email: pyry.gronholm@prosysopc.com
Tags: OPC UA, Security, Open Industry 4.0
comments powered by DisqusAbout Prosys OPC Ltd
Prosys OPC is a leading provider of professional OPC software and services with over 20 years of experience in the field. OPC and OPC UA (Unified Architecture) are communications standards used especially by industrial and high-tech companies.
Newest blog posts
Why Do Standards Matter in Smart Manufacturing?
The blog post discusses the importance of standards in smart manufacturing, envisioning a future where auto-configurable systems in manufacturing rely on standardized data formats for seamless integration and reduced costs, with a focus on the OPC UA standard family as a key enabler.
OPC UA PubSub to Cloud via MQTT
Detailed overview of the demo presented at the OPC Foundation booth
SimServer How To #3: Simulate data changes on a server using an OPC UA client
A two-part step-by-step tutorial on how to write data changes on an OPC UA server using an OPC UA client.